On February 16th, 2024, WRAL News Interviewed Stern Security’s CEO, Jon Sternstein, about AI, deepfakes, and election meddling. The interview discussed the current threat landscape, protective measures, and covered what big tech companies are doing to combat this issue. The interview also discussed positive aspects of AI. The full interview can be seen here: https://www.wral.com/video/cybersecurity-expert-explains-how-ai-could-meddle-in-elections/21288228/
System and Organization Control (SOC) reports have quickly become a standard request for SaaS application providers in order for customers to perform a security due diligence review. So, are all SOC reports the same? No! Should you read the SOC report? Absolutely! How should you properly review a SOC report? Read on 🙂 Background SOC […]
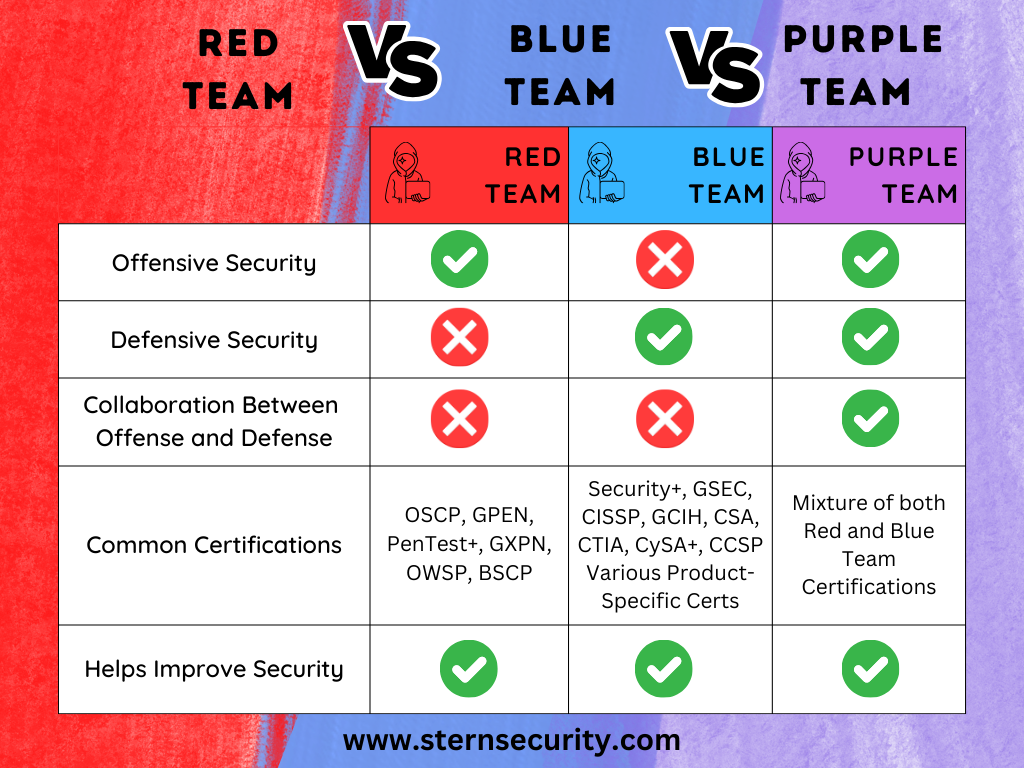
A well-run cybersecurity team operates like a beautiful orchestra, each individual knowing their part and contributing to the same goal. A cybersecurity team may consist of team members wearing numerous hats ranging from management, to defensive, and offensive security. The offensive team members will attack their own organization to find vulnerabilities so the other teams […]
Over the past year, news outlets have been buzzing about Facebook, now called “Meta”, collecting vast amounts of data from healthcare organizations and tax return companies. Some of these companies are announcing breaches as a result of this data collection. Why are Companies Sending Sensitive Data to Facebook? Let’s be clear – Companies are not […]
The 2022 Triangle InfoSeCon event hosted by Raleigh’s ISSA was on September 9th, 2022. To a full crowd, Stern Security‘s Founder & CEO, Jon Sternstein, gave a presentation titled: “Break Down Silos & Secure the Planet”. The presentation abstract was the following: People tend to cluster in their own silos and tribes in both society […]
In its second annual Velocity healthcare data breach report, Stern Security has critically analyzed over 5,000 data breaches since the Department of Health and Human Services (HHS) began tracking the information in 2009. Stern Security utilized data from their HealthcareBreaches.com website as well as published information from HHS to create this comprehensive study. Stern Security […]
What is 405(d) HICP? 405(d) Health Industry Cybersecurity Practices (HICP) is a healthcare cybersecurity framework created out of a congressional mandate from the Cybersecurity Act of 2015. Section 405(d) of this mandate has a goal to strengthen the cybersecurity posture of healthcare and public health sector. A collective called the 405(d) Task Force was formed from […]
Keeping up with Two-Factor Authentication Day (2/2/23), we decided to showcase some cybersecurity and compliance frameworks that recommend 2-factor authentication controls. The frameworks we reviewed include: Cybersecurity Framework References The multi-factor authentication controls within these frameworks are listed in the chart below. Framework Reference Control FFIEC CAT D3.PC.Am.B.9 Customer access to Internet-based products or services […]
WRAL TechWire, the leading technology news publication in the Carolinas, highlighted Velocity at the top of their Venture Connect conference coverage. Jon Sternstein, the Founder and CEO of Stern Security, took the stage at CED’s Venture Connect conference. He discussed how the Velocity SaaS product accurately evaluates cyber risk and uses this information to show […]
There are hundreds of cybersecurity products on the market and it can be difficult to select one between the noise. Do you select a cybersecurity product based on an alert you see on the news? Choose based on an advertisement or magazine article? Do you simply select one because it appears on a “magic quadrant”? […]