There are hundreds of cybersecurity products on the market and it can be difficult to select one between the noise. Do you select a cybersecurity product based on an alert you see on the news? Choose based on an advertisement or magazine article? Do you simply select one because it appears on a “magic quadrant”? […]
In April of 2023, CISA released version 2.0 of their Zero Trust Maturity Model. What is CISA? The Cybersecurity & Infrastructure Security Agency (CISA) is a U.S. federal agency that is responsible for strengthening cybersecurity across the government. The agency also provides resources for helping U.S. companies reducing cyber risk. What is Zero Trust? At […]
At Stern Security, we have declared February 2nd as Two-Factor Authentication Day! The date is 2/2 so naturally it’s the best day for this holiday. This is a day to spread awareness about 2-factor authentication which is one of the most important ways to protect your online accounts at home and at work. Using a […]
In its first annual healthcare data breach report, Stern Security has critically analyzed over 4,000 data breaches since the Department of Health and Human Services began tracking the information in 2009. Stern Security utilized data from their HealthcareBreaches.com website as well as published information from Health and Human Services to create this comprehensive report. This […]
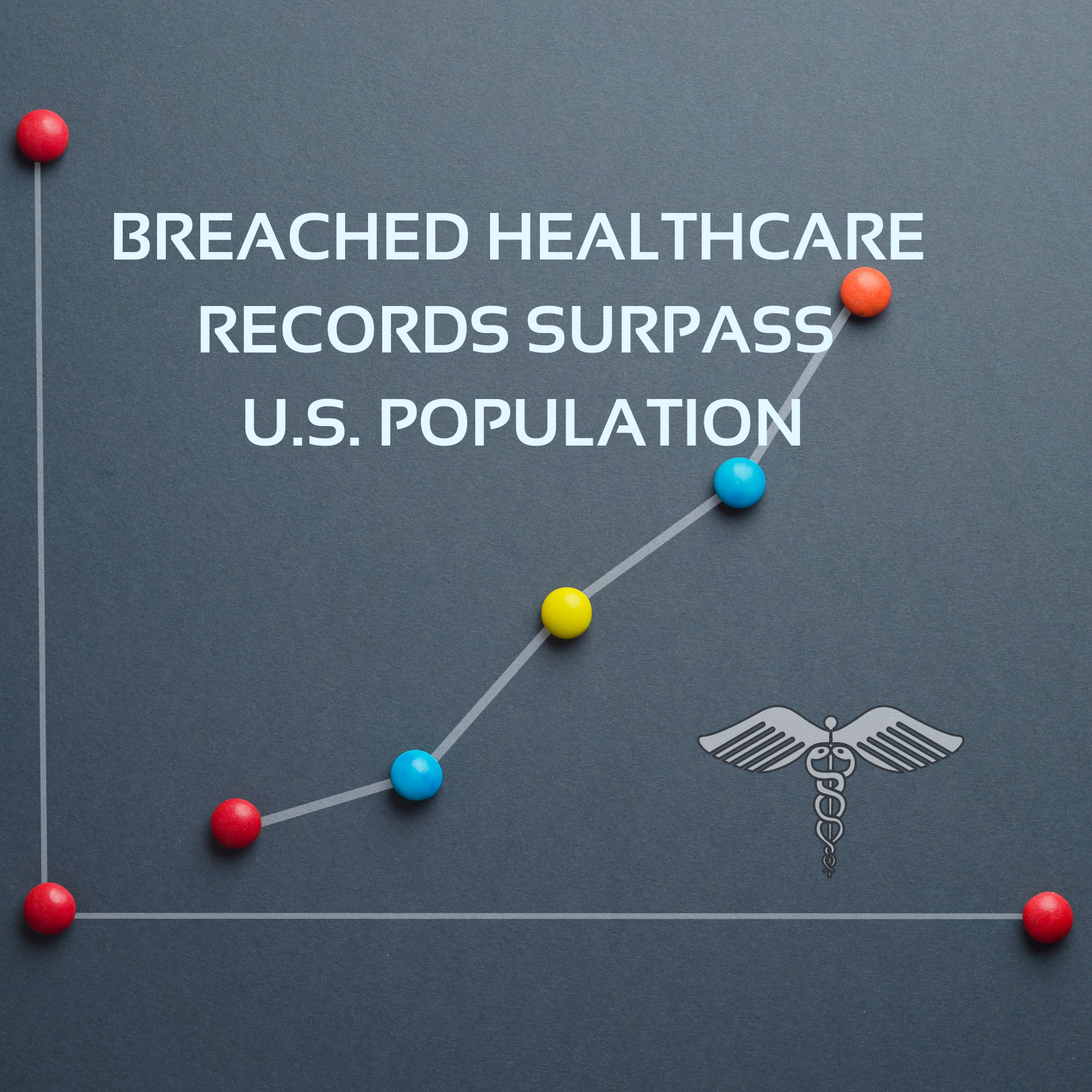
Healthcare breaches have recently reached a grim milestone. As of June 10th, 2022, the number of Protected Health Information (PHI) records breached has reached 341,995,928. To put in prospective, this number surpasses the United States population which is at 332,759,097 (United States Census Bureau, 2022). It must be noted that these numbers only include reported healthcare […]
Background Our company mission is to “Secure the Planet”. This means that we aim to provide education and solutions that any company in the world can use to reduce cyber risk. Our flagship product, Velocity, is a web application (SaaS product) which companies can use to evaluate their own cybersecurity posture as well as to […]
Introduction Not all vulnerability scans are created equal. The configuration of a vulnerability scan makes an enormous impact on your results. Authenticated vulnerability scans will provide much greater insight into an organization’s security posture than unauthenticated scans. However, there is a place for unauthenticated vulnerability scans. This article discusses the differences between authenticated and unauthenticated […]
Introduction Velocity helped a large hospital system quadruple the speed of third-party risk assessments, increase accuracy of reviews, create a continuous assessment process, and track internal risk using the Center for Internet Security (CIS), NIST Cybersecurity Framework (CSF), and the HIPAA Security Rule. Background The hospital was struggling to manually review hundreds of vendor (business […]
On November 4, 2021, to safeguard sensitive national security information, the Department of Defense (DoD) launched Cybersecurity Maturity Model Certification (CMMC) 2.0, a comprehensive framework to protect the defense industrial base (DIB) from increasingly frequent and complex cyberattacks. With its streamlined requirements, CMMC 2.0 was created to:• Cut red tape for small and medium sized […]
Background Technology has dramatically changed almost all aspects of human life, giving us amazing communication ability, a healthcare revolution, financial opportunities, and safe energy, all growing at exponential rates. These benefits become risks if the technology is not made secure. At Stern Security, our mission is to secure the planet, business by business, industry by […]