Stern Security’s CEO, Jon Sternstein discusses ransomware with WRAL News. See the full story here: http://www.wral.com/5oys-ransomware-story-for-thursday/16665496/
WRAL News Stern Security’s CEO, Jon Sternstein discusses internet privacy with WRAL News. See the full story here: http://www.wral.com/laura-brache/16592048/
Stern Security’s CEO, Jon Sternstein discusses hackable homes and the “Internet of Things” (IoT) with WRAL News. See the full story here: http://www.wral.com/strong-passwords-provide-good-defense-as-internet-of-things-grows/16511492/
Stern Security’s CEO, Jon Sternstein, was featured in Business North Carolina’s article titled “Internet privacy and cybersecurity round table: For your eyes only”. To see the online version of the article, follow this link: https://businessnc.com/internet-privacy-cybersecurity-round-table-eyes/. To view the full print version, order here: https://businessnc.com/archives/november-2016/
At the August 2016 NCHICA Annual Conference, Chuck Kesler (CISO, Duke Health) & Jon Sternstein (CEO, Stern Security) teamed up to present on the ransomware threat in healthcare.
2016 NC HIMSS Annual Conference Multifactor Authentication – 2016’s Essential Security ProjectDuke Health’s Chief Information Security Officer (CISO), Chuck Kesler, and Stern Security’s CEO, Jon Sternstein, teamed up to present on multi-factor deployment strategies at the 2016 NC HIMSS Annual Conference. Date: April 20 & 21, 2016 Location: Hilton North Raleigh/Midtown Hotel3415 Wake Forest Rd, […]
We have compiled a list of security measures to implement to either prevent ransomware or limit the damage. Organizations need not implement all of these in order to prevent ransomware. However, these are various strategies that can be implemented depending on the company. Security measures such as “application whitelisting” will prevent most malicious software on […]
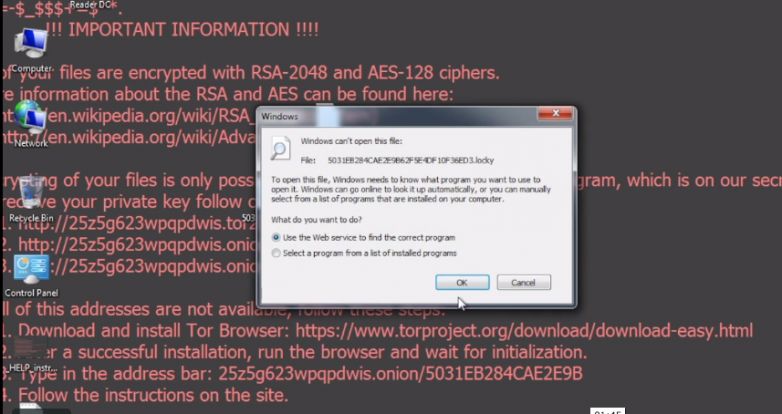
Stern Security Labs analyzed a Locky ransomware sample. The following video shows an actual Locky ransomware attack on a Windows 7 machine. Watch how fast the ransomware encrypts the files on the computer. The computer is encrypted within one minute of clicking on the malicious “invoice.pdf” file! Ransomware attack demonstration from Stern Security on Vimeo.
In February 2016, PenTest Magazine’s was dedicated to “Cloud Pen testing”. This special edition featured an article by Stern Security’s Founder, Jon Sternstein. Here is an excerpt from the article: “A pair of eyes intently stares at the computer screen while ten fingers are furiously typing on the keyboard. The penetration tester smiles as he […]
We have recently received two samples of Locky maldoc (malicious document) ransomware from a healthcare institution. Ransomware is a devastating piece of malware that encrypts important files on an infected computer and demands ransom to decrypt the files. We will examine two samples. Both samples arrived via email and were not detected by spam filters […]