In April of 2023, CISA released version 2.0 of their Zero Trust Maturity Model.
What is CISA?
The Cybersecurity & Infrastructure Security Agency (CISA) is a U.S. federal agency that is responsible for strengthening cybersecurity across the government. The agency also provides resources for helping U.S. companies reducing cyber risk.
What is Zero Trust?
At a high level, Zero Trust is a cybersecurity methodology that assumes a breach can occur at any time. As such, each resource should have the least amount of privileges needed to perform their job and should be continuously authenticated to confirm authorization. The National Security Telecommunications Advisory Committee (NSTAC) describes Zero Trust as a cybersecurity strategy that treats every resource as untrusted. While most other security models use the location of an individual or device as a means to provide access, Zero Trust focuses on the data that is being accessed.
CISA Zero Trust Overview
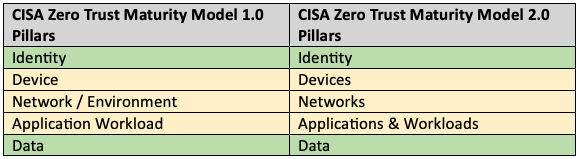
CISA states that their maturity model is not the only way to accomplish Zero Trust. However, CISA’s model is clear, concise, possibly the easiest model to understand, and CISA has a strong reputation for solid recommendations. In CISA’s Zero Trust Maturity Model, there are five pillars, or categories, that contain controls for moving towards a Zero Trust Architecture. The five pillars are Identity, Devices, Networks, Applications & Workloads, and Data as shown in the image below.
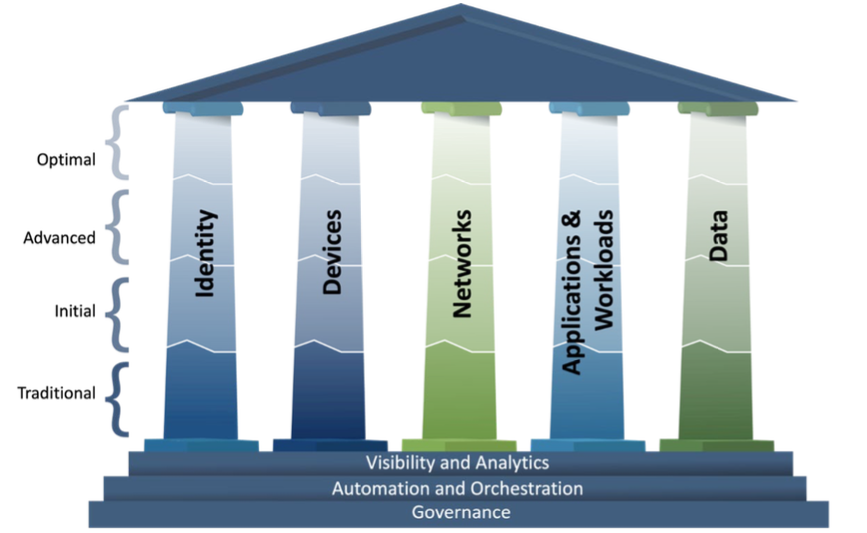
There are a total of 36 security controls, or “functions” as CISA calls it, across all of the pillars. While there are unique security controls for each pillar, there are three control types that are within each pillar. These three control types that are cross-cutting through each pillar are Visibility and Analytics, Automation and Orchestration, and Governance. The cross-cutting controls can be used to coordinate implementation and interoperability of functions across the pillars.
The CISA Zero Trust model contains four maturity stages for each of the 36 security controls. Organizations start with the Traditional stage and move to Initial, Advanced, and finally Optimal. Each maturity stage provides an increasing level of protection and adoption complexity.
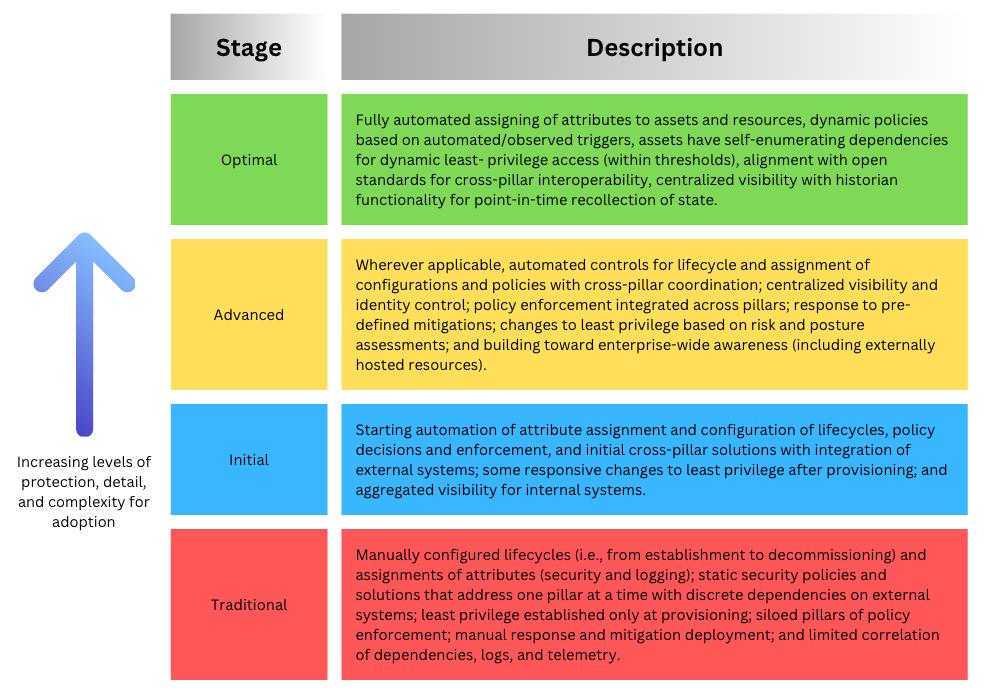
Implementation Challenges
Implementing Zero Trust is not a trivial task. There are 36 major functions that need to be optimized before achieving the highest maturity level. This is a process that will most likely take years for an organization to complete. Some of the challenges with implementing Zero Trust are:
- Cost – An organization will probably need to purchase new security tools and hire additional staff to reach the higher levels of maturity. For example, an organization may have multi-factor authentication (MFA) with SMS (text message), but the more mature levels require “phishing-resistant MFA” such as Yubikeys or Feitian USB security keys. Purchasing the security keys and educating staff can be costly.
- Time – It takes time to implement each of these security measures. This includes both implementation time and employee education time.
- Process Change – There are numerous challenges to implementing new processes. Taking our MFA implementation example, an organization will need to change how they perform multi-factor authentication across the organization.
- Legacy Systems – Many legacy systems were not designed with security in mind. These legacy systems may implicitly trust everyone, or have a single shared account.
CISA describes the Zero Trust implementation as a journey. Each stage of this journey requires more levels of effort while achieving greater protection.
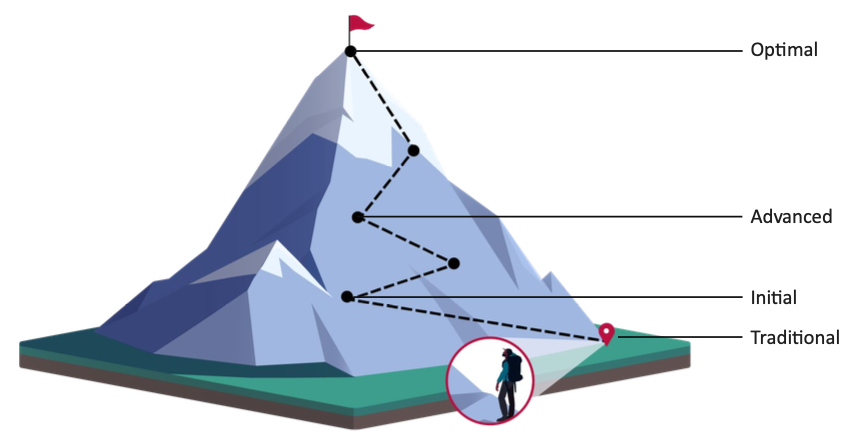
Benefits of Zero Trust
Moving towards higher levels of maturity within Zero Trust have enormous security benefits which is why organizations strive to achieve this goal. At the Optimal maturity level, the risk of a security breach is minimized. Zero Trust can also help companies achieve compliance goals by moving well beyond the initial compliance requirements. There are also customer and business benefits as an organization with a higher level of security earns more trust from its customer base.
Changes from CISA Zero Trust v1.0 to v2.0
CISA has made a number changes from their Zero Trust maturity model 1.0 released in 2021 to version 2.0 that was released in April of 2023.
Moving from Three to Four Maturity Stages
The largest change is moving from three to four maturity stages. As CISA states, the Zero Trust Maturity Model is a journey which will most likely take time to implement. Having more stages provides greater insight into an organization’s progress.

Pillar Changes
There are still five pillars within the CISA Zero Trust Maturity Model 2.0, however the naming has changed slightly.
Security Functions within Pillars
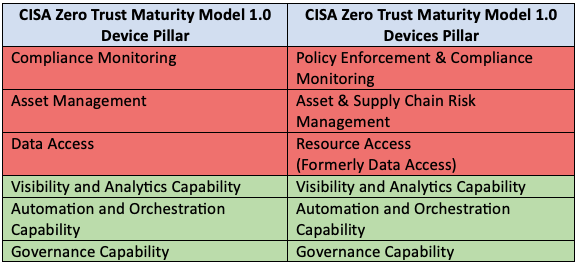
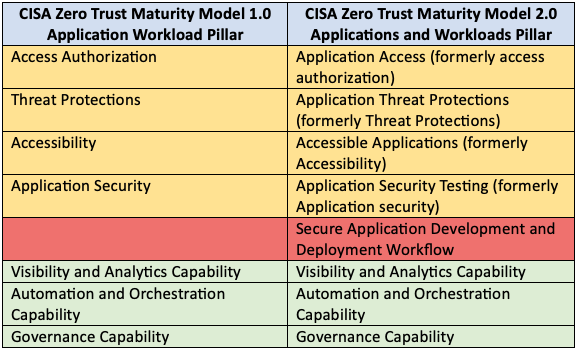
The CISA Zero Trust Maturity Model has moved from 31 security controls (called “Functions” within the model) to 36 controls. The changes are listed below and grouped by each of the five pillars.



Velocity Can Help with the CISA Zero Trust Maturity Model Journey
At Stern Security, we have added the CISA Zero Trust Maturity Model into our Velocity platform. Any organization can easily map their Zero Trust journey within Velocity. Try Velocity for free today.
Conclusion
The 2.0 version of CISA’s Zero Trust Maturity Model is a well-organized and highly regarded framework to follow in order to achieve Zero Trust goals. Increasing an organization’s Zero Trust maturity is a journey that will take time and resources, but will greatly reduce cybersecurity risk. CISA’s model is a recommended approach for completing an organization’s Zero Trust goals.
Works Cited
Cybersecurity and Infrastructure Security Agency Cybersecurity Division. (2021, June). Zero Trust Maturity Model: Pre-decisional Draft Version 1.0. CISA.gov.
Cybersecurity and Infrastructure Security Agency Cybersecurity Division. (2023, April). Zero Trust Maturity Model: Version 2.0. CISA.gov.





