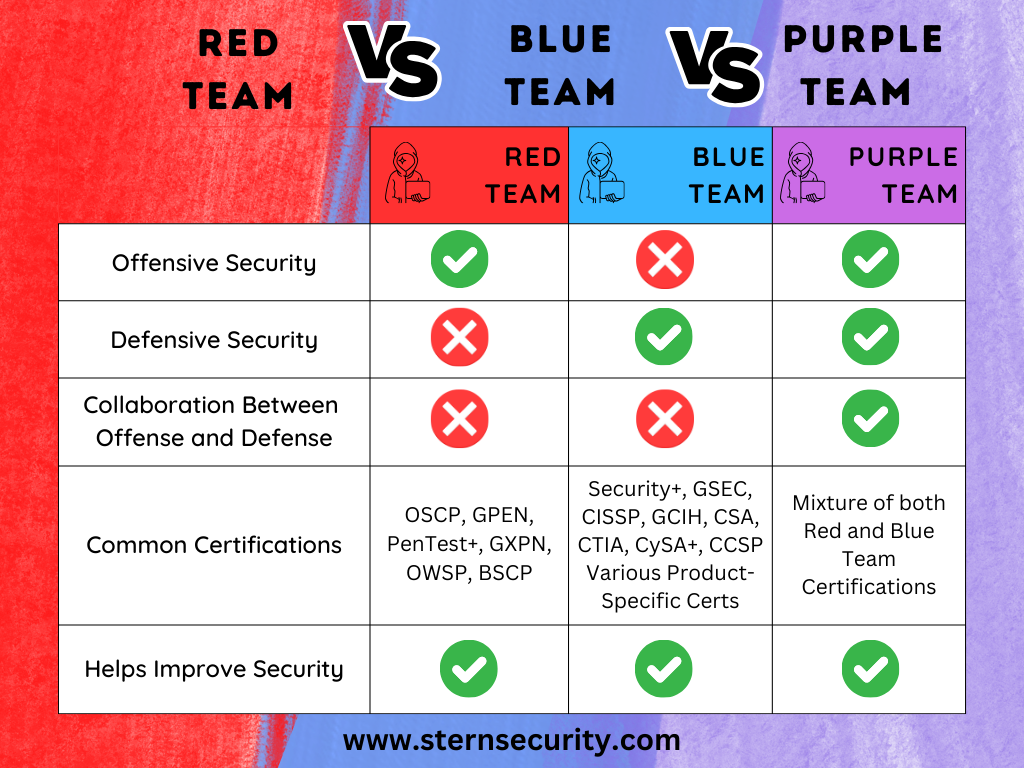
A well-run cybersecurity team operates like a beautiful orchestra, each individual knowing their part and contributing to the same goal. A cybersecurity team may consist of team members wearing numerous hats ranging from management, to defensive, and offensive security. The offensive team members will attack their own organization to find vulnerabilities so the other teams can resolve the issues. The defenders will deploy security software and hardware to shield the organization from attack. Cybersecurity professionals have given color codes to roles within the security orchestra including “Red Team”, “Blue Team”, and “Purple Team”. So what is the difference between a Red Team, a Blue Team, and a Purple Team in cybersecurity? At a high level, the Red Team focuses on offensive security (attacking), the Blue Team works on defending the organization, and the Purple Team is a collaborative effort between the Red Team and Blue Team.
Red Team Details
The Red Team performs the offensive security functions within the organization. In other words, the Red Team mimics Tools Tactics and Procedures (TTPs) of real attackers to discover vulnerabilities, exploit them, and gain access to data. The Red Team is comprised of penetration testers (ethical hackers). The Red Team will provide the organization with reports of the discovered vulnerabilities. Members of the Red Team often have cybersecurity certifications geared towards penetration testing. Some of the common certifications for Red Teamers include:
- OSCP (Offensive Security Certified Professional)
- GPEN (SANS GIAC Penetration Tester)
- PenTest+ (from CompTIA)
- GXPN (GIAC Exploit Researcher and Advanced Penetration Tester)
- Offensive Security Wireless Professional (OSWP)
- Burp Suite Certified Practitioner (BSCP)
Blue Team Details
The Blue Team performs the defensive security measures within the organization. They utilize tools and strategies such as SIEMs (Security Information Event Management systems), IPS/IDS (Intrusion Prevention System / Intrusion Detection System), Firewalls, NAC (Network Access Control), Endpoint Protection, File Permissions Restrictions, DLP (Data Loss Prevention), Email Protection, Security Awareness Training, and more. Blue Team members have a wide area of knowledge in order to defend the organization from attack.
Some common certifications on the Blue Team side include, but are not limited to:
- CompTIA Security+
- GIAC Certified Incident Handler Certification (GCIH)
- GIAC Security Essentials (GSEC)
- Certified Cloud Security Professional (CCSP)
- Certified SOC Analyst (CSA)
- Certified Threat Intelligence Analyst (CTIA)
- Certified Cyber Forensics Professional (CCFP)
- CompTIA Cybersecurity Analyst (CySA+)
- Systems Security Certified Practitioner (SSCP)
- Certified Information Systems Security Professional (CISSP)
- Various product-specific certifications
Purple Team Details
The Purple Team is generally a collaborative effort between the Blue Team and the Red Team. The Red Team may walk through various stages of an attack using a framework such as MITRE ATT&CK. At the same time, the Blue Team will see which attacks are discovered or blocked and make changes as appropriate. This collaborative effort between teams helps streamline improvements to the security posture. Another positive outcome from the teams working together, is that instead of feeling bad when an attack succeeds or fails, both teams are learning from each other and understand that they are working towards the same goal.
How Can Stern Security Help?
Stern Security has extensive experience working with organizations on Purple Team engagements. The company emulates known threat actors using their Tools Tactics and Procedures (TTPs) to work through the various stages of an attack as charted within the MITRE ATT&CK Framework. Stern Security works with an organization’s Blue Team to see which attacks are discovered, blocked, and which attacks bypass defenses. Our team also helps Blue Teams design defenses to block similar attacks in the future. To top it off, Stern Security gives the Blue Team kudos for all mitigated attacks. Expert penetration testing services are a popular service offering by our organization. Stern Security’s Velocity application can be used to perform internal risk assessments, identify gaps, and view actionable recommendations to improve security.
Conclusion
Within a cybersecurity team, Blue Teams are defensive, Red Teams are offensive, and Purple Teams are a collaborative effort between the Blue and Red Teams. Individuals within these groups may have different skillsets and certifications, but they are all working towards reducing risk within the organization.