If the SolarWinds hack taught us anything, it’s that the security of a company’s infrastructure is dependent on the resilience of their vendors. A breached vendor is a trojan horse that bypasses normal defenses and accesses the trusted areas of the network. Threat actors have cunningly discovered that a trusted vendor is often the easier path to infiltrate their primary target. Some of the top cybersecurity technologies in 2021 focus on vendor risk evaluation.
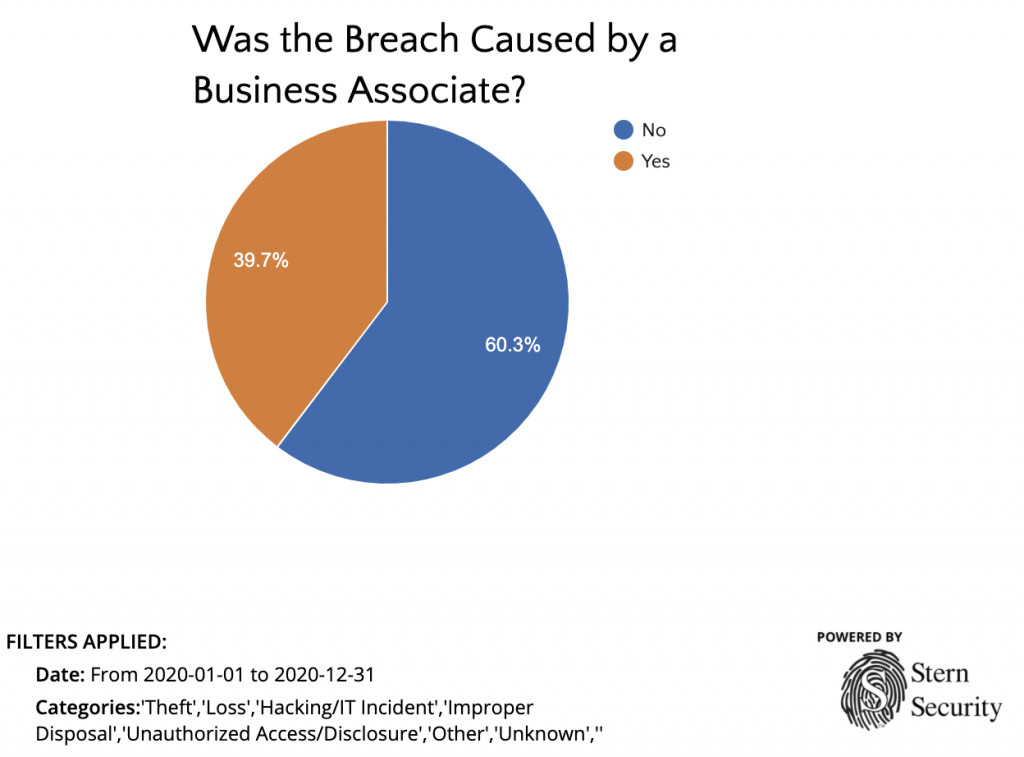
Even if companies have internal security teams, evaluating vendor risk is a resource intensive process. Most organizations utilizing spreadsheets to create vendor questionnaires. After several back-and-forth emails and several weeks, the vendor completes the questionnaire. Next, begins an equally long process of internal deliberations to give the vendor a risk score. This process can take months for a single vendor. The current vendor security review process that most organizations perform is inefficient and varies in accuracy. Meanwhile, vendor breaches continue to skyrocket. In the healthcare industry, 21.1% of breaches were caused by vendors (business associates) from 2009 to December 31st of 2019. However, in 2020, breaches from vendors spiked to 39.7%!

Vendor breaches in the healthcare industry greatly increased in 2020:
A strong vendor risk evaluation solution is critical to combat these issues. A good vendor risk management product adds efficiencies, reduces cost, and increases security for organizations and vendors. These solutions automate much of the manual work and consolidate the vendor evaluations into a few places. Instead of every single customer performing their own evaluations, these solutions perform the work. These solutions can evaluate hundreds of vendors at once instead of the inefficient spreadsheet questionnaire evaluations and countless vendor security meetings that many organizations perform today. Internal vendor evaluations will become a process of the past and replaced by vendor risk management solutions.
Vendor security should be evaluated before the contract is signed. Vendors have incentive to strengthen security if their customers are grading them as part of the product evaluation and contract negotiation. If they want the business, they better have good security.
This field continues to grow rapidly as vendor breaches spike in frequency. Vendor risk management solutions will help combat this issue and shine the spotlight on third-party security. Without a doubt, this is one of the top cybersecurity segments in 2021. Proper vendor evaluation is needed to increase security and reduce risk.





