Introduction
Imagine building a strong, stable fortress around your most important assets. All of your focus is on stopping the intruder that will directly target your organization. However, there is an indirect way to breach the gates – through your third parties. Your organization relies on third parties (vendors) for necessary services and you have given them all keys to the castle so they can freely walk in and out like one of your employees. In many cases, you trust them to hold and manage your critical assets for you. Do you believe that they have created a fortress around your data that is as strong as the fortress that you created?
A company’s own internal cybersecurity posture should be the initial focus for protecting any organization. However, vendor risk is close behind. In today’s world, no organization operates in isolation. Every organization relies on third parties to conduct business whether it is for a customer platform, email service, banking, patient portal, infrastructure, deliveries, and more. These third parties are truly an extension of your own organization and they can either increase or decrease your security posture.
Problem
The vendor risk management problem is well known as we’ve seen major organizations announce breaches that originated through their third parties. In industries that publicly list their breach data, we can clearly see how serious and extensive this problem really is. Take the healthcare industry as an example – From 2009 to 2019, between 20% and 24% of data breaches were attributed to third parties or business associates. However, in 2020, breaches by business associates spiked to 40.2%!! There are similar examples in every industry in which organizations rely of third parties. The recent SolarWinds breach is a prime example of this as government entities and major corporations were impacted.
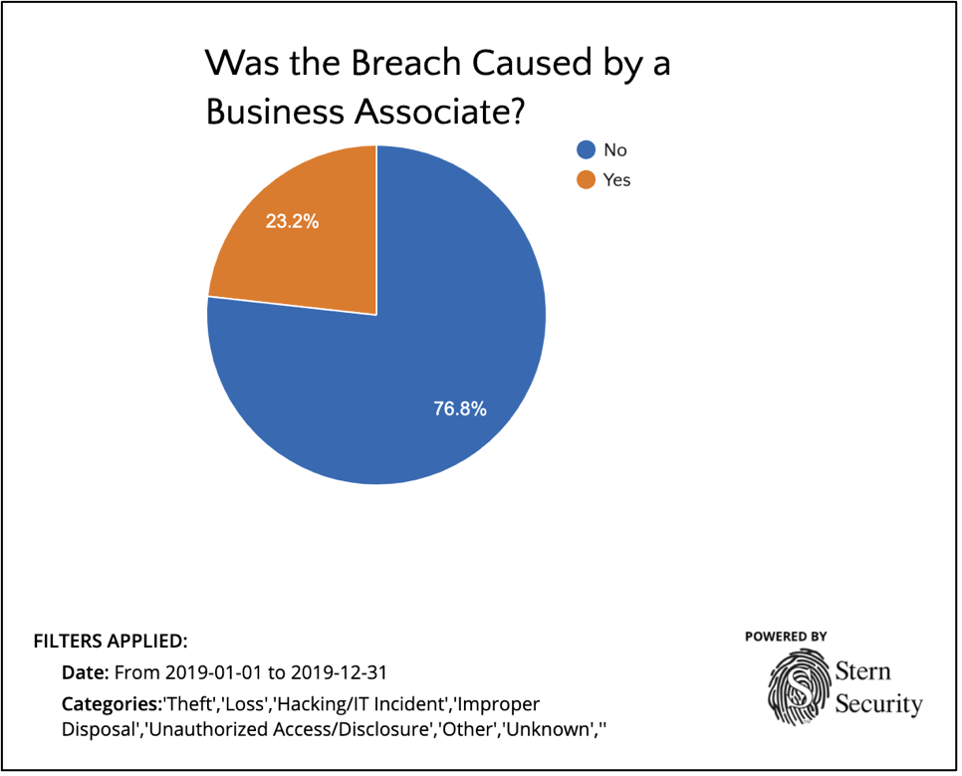
Third Party breaches in the healthcare industry in 2019 (Source: HealthcareBreaches.com)
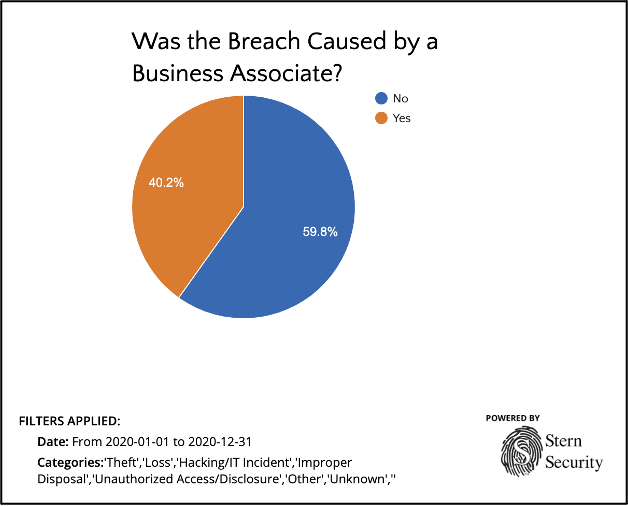
Third Party breaches in the healthcare industry in 2020 (Source: HealthcareBreaches.com)
Regulations
Regulations have tried to stay ahead of third party security, but for many, if not most, organizations, the 3rd party security review is still not a mature process.
FFIEC and Gramm-Leach-Bliley Act (GLBA)
Over 20 years ago, GLBA (also called the Financial Modernization Act of 1999) tried to address the issue of internal and third party vendor risk to customer data for financial institutions. Buried deep inside this regulation is SEC. 501. PROTECTION OF NONPUBLIC PERSONAL INFORMATION. SEC 501(b), labeled, “Financial Institutions Safeguards” in essence states that each financial institution has an obligation to protect the security and confidentiality of customer data (106th Congress, 1999).
The FFIEC (Federal Financial Institutions Examination Council) IT Examination Handbook further states that financial organizations should ensure that service providers, or third parties, which have access to customer data adhere to GLBA SEC. 501(b) regulations (FFIEC, n.d.).
NCUA
Credit Union auditors are becoming more experienced when it comes to 3rd party security. The National Credit Union Administration (NCUA) examiners review third party due diligence procedures as part of their audits (Young LaBerge, 2019). This should not come as a surprise to credit unions as a 2007 NCUA Supervisory Letter detailed evaluating third party relationships. Specifically, this letter stated that examiners should review the following with respect to credit union third party relationships commensurate with the risk profile: Risk Assessment and Planning, Due Diligence, Risk Measurement, Monitoring and Control (NCUA, 2007).
23 NYCRR 500
New York State has also attempted to manage the cybersecurity issues in the financial industry including those posed by third parties. The New York State Department of Financial Services enacted “Cybersecurity Requirements for Financial Services Companies” also known as 23 NYCRR 500, which went into effect on March 1st, 2017 (NEW YORK STATE DEPARTMENT OF FINANCIAL SERVICES, 1). The regulation states that each covered entity (Financial Services Organizations) must assess the risks that their Third Party Service Providers poses to their data. It goes on to state that Covered Entities had until March 1st, 2019 to complete a thorough due diligence process on all Third Party Service Providers (NY Dept of Financial Services, 2020). In addition to the initial review of the third parties, section 500.11 “Third Party Service Provider Security Policy” states that Covered Entities are required to perform periodic assessments of Third Party Service Providers based on “the risk they present and the continued adequacy of their cybersecurity practices” (NEW YORK STATE DEPARTMENT OF FINANCIAL SERVICES, 1).
HIPAA & HITECH
The Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, laid the groundwork necessary for healthcare organizations to secure Protected Health Information (PHI) through the HIPAA Security Rule. However, for third parties (Business Associates), HIPAA Compliance was not strong, criminal enforcement was not in place, and breach notification rules were not in scope. It wasn’t until 2009 when the Health Information Technology for Economic and Clinical Health Act (HITECH) was enacted which fully brought Business Associates into the security requirements and notifications within HIPAA Compliance (HIPAA Journal, n.d.).
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is one of the latest additions to the cybersecurity third party risk arena. This certification is based on both NIST 800-171 and DFARS 252.204-7012. CMMC was developed by the Department of Defense (DoD) to strengthen the cybersecurity posture of defense contractors. All defense contractors must at least have CMMC Level 1 certification, but the levels increase depending on the sensitivity of data involved.
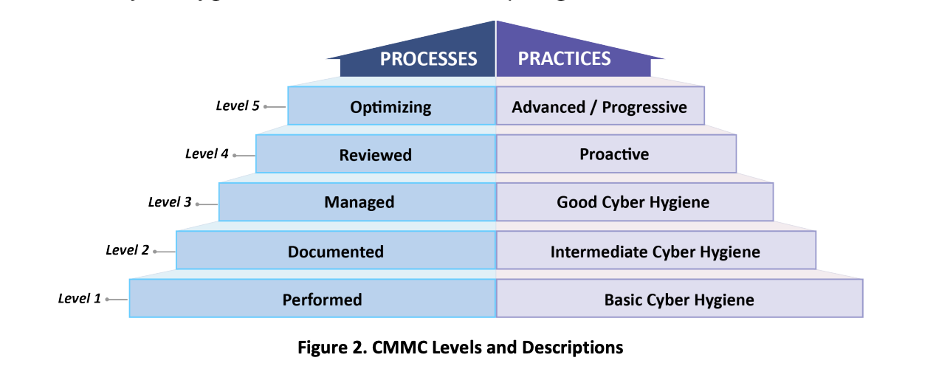
CMMC Levels (Carnegie Mellon University and The Johs Hopkins University Applied Physics Laboratory LLC, 2020)
Current Review Process
Many organizations do not review the security posture of their third parties. Covered Entities often rely on contractual language asserting that their vendors must “protect” the data involved. However, looking into whether the vendor is actually protecting the data requires both time and security expertise. If a covered entity does review their third party controls, it usually only involves asking for a SOC 2 Type 2 or similar report. Some organizations take it a step further by sending self-created security questionnaires in PDF or Excel formats to their third parties during contract negotiations. This data is then reviewed and discussed in numerous meetings which result in a final report that may be created months after the initial discussions.
Solutions
There are various solutions in place that offer vendor security assessments services, but few are accurate. Our team at Stern Security created a game changing cloud application called Velocity (https://www.velocitysec.com) to address this issue head-on and make the entire vendor review process simple for customers. Our cloud-based solution is both efficient and accurate. Additionally, our team verifies vendor supplied data in the system which goes well beyond commonly used self-assessment questionnaires.
Take a look at how Velocity helps companies manage their security posture and third party vendor risk
Conclusion
Regulatory bodies and auditors are catching onto the risk of third parties. Organizations are also beginning to ask the right questions before handing the keys to the castle to vendors. Cutting edge solutions like Velocity make the vendor review process straightforward, rigorous, thorough, and trustworthy. We still have a long road ahead to ensure that vendors create fortresses that are as strong as or even stronger than the ones their customers build to protect the most valuable assets.
Book a Demo of Velocity
Works Cited
106th Congress. (1999, November 12). GRAMM–LEACH–BLILEY ACT. Retrieved from Congress.gov: https://www.congress.gov/106/plaws/publ102/PLAW-106publ102.pdf
Carnegie Mellon University and The Johs Hopkins University Applied Physics Laboratory LLC. (2020, 30 1). Cybersecurity Maturity Model Certification (CMMC). Retrieved from Office of the Under Secretary of Defense for Acquisition & Sustainment: https://www.acq.osd.mil/cmmc/docs/CMMC_Model_Main_20200203.pdf
FFIEC. (n.d.). Vendor and Third-Party Management . Retrieved from FFIEC IT Examination Handbook Infobase: https://ithandbook.ffiec.gov/it-booklets/retail-payment-systems/retail-payment-systems-risk-management/operational-risk/vendor-and-third-party-management.aspx
HIPAA Journal. (n.d.). HIPAA and HITECH . Retrieved from HIPAA Journal: https://www.hipaajournal.com/hipaa-and-hitech/
NCUA. (2007, October). Supervisory Letter No 07-01: Evaluating Third Party Relationships. Retrieved from National Credit Union Administration: https://www.ncua.gov/files/letters-credit-unions/LCU2007-13ENC.pdf
NEW YORK STATE DEPARTMENT OF FINANCIAL SERVICES. (1, March 2017). CYBERSECURITY REQUIREMENTS FOR FINANCIAL SERVICES COMPANIES. Retrieved from governor.ny.gov: https://www.governor.ny.gov/sites/governor.ny.gov/files/atoms/files/Cybersecurity_Requirements_Financial_Services_23NYCRR500.pdf
NY Dept of Financial Services. (2020, 12 10). FAQs: 23 NYCRR Part 500 – Cybersecurity . Retrieved from New York State Department of Financial Services: https://www.dfs.ny.gov/industry_guidance/cyber_faqs
Young LaBerge, E. M. (2019, April 12). Rumor Has It: NCUA Digging Deeper on Vendor Management. Retrieved from National Association of Federally-Insured Credit Unions (NAFCU): https://www.nafcu.org/compliance-blog/rumor-has-it-ncua-digging-deeper-vendor-management





