The September 2017 (Volume 15 Issue 9) edition of the ISSA Journal features an article by our Founder and Principal, Jon Sternstein. The title of the story is “Healthcare Security Ailments and Treatments the World Needs to Know” and provides valuable insight into healthcare data breaches.
All of the graphs shown can be recreated on our Healthcare Breach Executive Dashboard at https://www.healthcarebreaches.com. Here is the article as published on ISSA’s September 2017 edition:
Healthcare Security Ailments and the Treatments the World Needs to Know – Jon Sternstein – ISSA Member, Raleigh Chapter
This article provides insight into the immense data breach problem affecting the healthcare industry. It also analyzes healthcare breach trends and shows how the threat landscape is changing in recent years. It proceeds to discuss a case study of a 2017 healthcare data breach in which the Protected Health Information (PHI) went up for sale on the dark market. The discussion closes with actionable solutions that all healthcare organizations should be accomplishing to minimize the risk of data breach.
The Epidemic
174,635,373. That is the total number of healthcare records that have been lost in U.S. breaches from 2009 until July 13th, 2017#6. Think about that for a minute. 174 million Protected Health Information (PHI) records is a number so large, it is difficult to comprehend. The entire United States population is only 321.4 million individuals. The most populous state, California, is only 39 million individuals, a number that is dwarfed by the number of patient records lost since 2009. This large number only includes breaches that are 500 or more records. This is a large problem and it is going to take a significant effort to stop this trend.
Your patient record contains your full name, Social Security Number (SSN), address, phone number, birthdate, medical condition, family information, and more. Unlike payment card data, Protected Health Information (PHI) cannot be replaced or reissued. This makes healthcare breaches the most costly out of any industry. Ponemon’s 2017 Cost of Data Breach Study lists healthcare breaches at a staggering $380 per record lost, a number that continues to increase each year#13. Healthcare breaches cost $135 more per record than the next closest industry. The average data breach size in the 2017 Ponemon study was 24,089 which would cost a healthcare organization $9,153,820 (24,089 x $380). Not only are these breaches costly to the organization, but they also impact the patients. The victims in these cases are people that trust the healthcare organization with their lives and their most sensitive information. They should not be troubled with identity theft on top of medical issues.
Breach Trends
Health and Human Services (HHS) categorizes healthcare breaches into five main groups: Hacking/IT Incident, Improper Disposal, Loss, Theft, and Unauthorized Access/Disclosure. Each of these categories can be summarized as follows:
Hacking/IT Incident: An intruder breaks into a computer system containing patient information. Or a server is misconfigured and allows remote access to patient data.
Improper Disposal: The insecure disposal of patient information. Examples include recycling paper healthcare records without shredding first. Another example is donating computers without securely erasing (or destroying) the hard drives.
Loss: Unintentionally misplacing patient information. A common example is a physician losing an unencrypted flash drive with patient information.
Theft: Physically stealing patient information.
Unauthorized Access/Disclosure: An individual accesses information they did not have authorization to view. Examples include patient records sent to the incorrect individual or a healthcare employee that views the healthcare records for patients that are not under their care. Some of the breaches in this category could be interpreted as Hacking/IT Incident breaches.
Since 2009, most of the reported healthcare breaches have been due to theft. Many of these theft breaches have occurred because unencrypted laptops or flash drives were stolen. It is difficult to eliminate theft of computer equipment, however, most of these breaches would not need to be reported if the affected organization simply encrypted their drives. Both Microsoft and Mac OS offer completely free full disk encryption with their operating systems so there really isn’t any reason why this protective measure is not in place. We can almost eliminate this risk with completely free solutions.
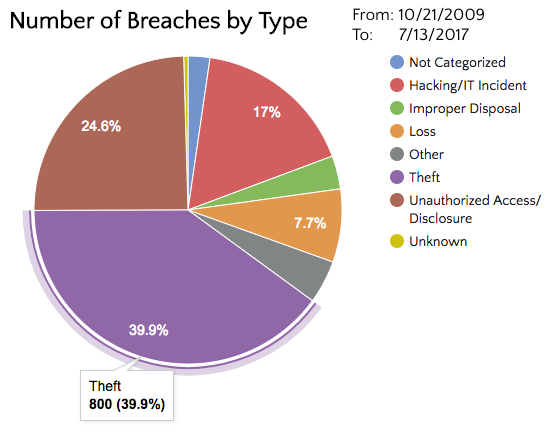
While it is clear that most of the reported healthcare breaches since 2009 have been due to theft, this trend is drastically changing. It would be a grave mistake to only focus on encrypting drives in order to protect patient information. Over the past two years, Hacking/IT Incident and Unauthorized Access have both passed Theft as the top causes of healthcare data breaches. Additionally, breaches due to theft have been declining.
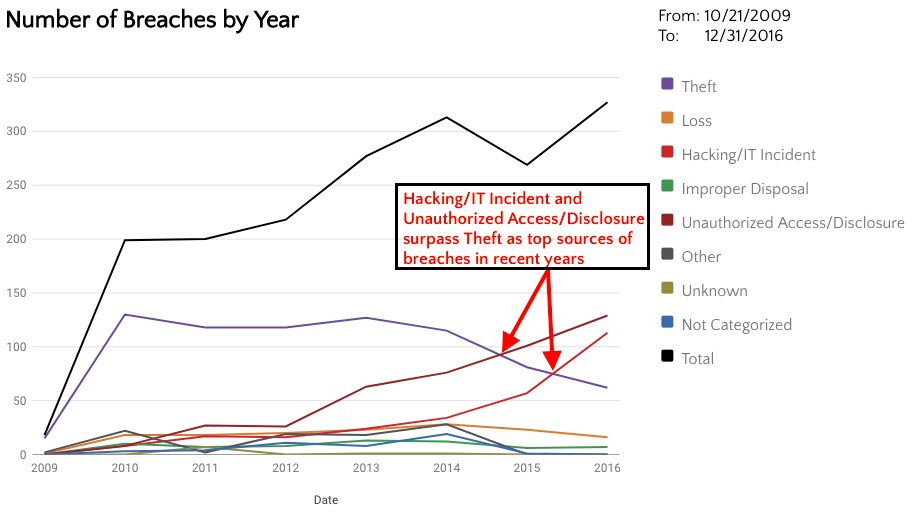
There are several reasons for these trends. First let’s examine why breaches due to theft are declining. Organizations are getting better at encrypting hard drives, thus reducing the amount of reportable breaches due to theft. This may also explain the decrease of breaches due to “loss” as well. However, organizations need to remember to encrypt laptops, desktops, and flash drives, not just laptops. There are still a large number of paper records stolen. Theft will continue to be a large threat while there are unencrypted devices and paper records available.
The increase in Hacking and Unauthorized Access/Disclosure breaches could be due to more attacks occurring and increasing reliance on technology to manage our healthcare data. We may also see more reportable breaches due to these categories because we’re simply getting better at detecting these types of incidents. So hacking is probably increasing, but we’re also getting better at discovering these compromises as they occur.
Patient Data for Sale
Why would anyone want to steal patient information? This is a question that I was asked many times when I was a healthcare security officer. People can generally see why a thief would steal cash or a credit card, but what can they do with a patient record? Since Protected Health Information (PHI) is your full identity, a thief could use that information to open new credit cards, make false insurance claims, sell for ransom, and more. Let’s look at a recent real life example. In March of 2017, a behavioral health center was hacked in Maine, USA. This breach was unique in that the PHI immediately appeared for sale on the dark web. The criminal stated that they had the PHI for 4229 individuals and the information contained names, addresses, phone numbers, employers, birthdays, social security numbers, and therapy notes. In addition to the listing the price, the criminal stated that the stolen data could be used for ransom and specifically noted the breached health provider’s $4 million insurance policy. The thief further implied that the data could be used to target affected individuals as the data contained full psychiatric information on “everyone from bank presidents to garage mechanics”#3. The criminal was selling the data for a minimum of $10,000 for the full set or $3 per individual’s name, address, date of birth, and social security number. This case is a prime example of how stolen Protected Health Information (PHI) is used and shows how criminals have complete disregard for how this information can affect the lives of the individuals. Healthcare data is incredibly sensitive and it is unfortunately being compromised at an alarming rate.
The Perfect Storm – Ransomware
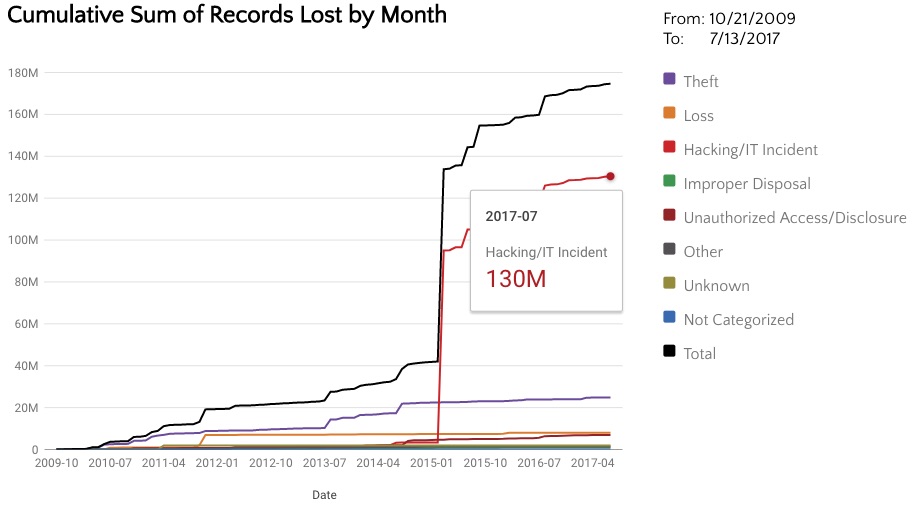
As if the previous threats were not enough, the healthcare industry has been slammed by ransomware. Not only have there been many reported healthcare ransomware breaches, the media has covered several cases where complete hospital systems have been overrun by ransomware and had to revert to paper records. Hollywood Presbyterian Medical Center#1 and Methodist Hospital in Kentucky#11 are just two examples of hospitals that were in a state of emergency due to ransomware and reverted to paper records while regaining access to their computers. In some cases, patients had to be redirected to other hospitals. This unfortunate trend is only increasing. In 2016, there were 10 reported healthcare breaches of 500 or more records due to ransomware#6. Halfway through 2017, we have already surpassed 2016’s number of reported ransomware breaches. This has been such a large problem that Health and Human Services released a ransomware fact sheet to help healthcare organizations#7. With ransomware on the rise, and system compromises becoming more prevalent, it’s no wonder why most patient records have been lost due to hacking and IT incidents. There is really no comparison between the amount of records lost due to hacking and all other breach types combined. Breaches due to hacking are usually larger because more data can be stolen when an entire server or database is compromised as opposed to the theft of a single laptop.
Regulatory Assistance
In order to protect health information, the U.S. government issued the HIPAA (Health Insurance Portability and Accountability Act of 1996) Security Rule#4. This lengthy document contains a list of steps that covered entities (such as hospitals) and their business associates must follow. One major requirement included in the Security Rule is HIPAA Part No. §164.308(a)(1)(ii)(A), the Risk Analysis. This requires organizations to “Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity”. All healthcare organizations both large and small must abide by these regulations. This is of such importance that the U.S. government has issued millions of dollars in fines for organizations that fail compliance for reasons such as failing to complete a risk analysis, or not signing a business associates agreement with a partner#9. In April of 2017, U.S. Department of Health and Human Services, Office for Civil Rights (OCR) publically announced a $2.5 million settlement with CardioNet for non-compliance with the HIPAA Security Rule and failing to have a Risk Analysis performed#5. If there were questions about HIPAA enforcement before, you don’t hear them now.
The Needed Treatment
At the end of the day, it is our duty as security professionals to protect the information that we are responsible for. The healthcare industry is no exception to this rule and in many ways, it contains some of the most sensitive information that we can protect. As the breach trends reflect, we have some serious work to do in healthcare and patients are expecting us to secure their data. Healthcare breaches affect each and every one of us. However, all is not lost and we can see from the decrease in breaches due to theft that is possible to lower risk in healthcare organizations. Here are some solutions that lower the risk of healthcare data breaches:
1. Security Strategy – All organizations need a strategy to successfully mitigate threats. A security strategy provides direction to a security program and allows the organization to measure progress and maturity. Many organizations make the mistake of purchasing security products without a complete strategy and then wonder why there are still security problems. A recommended method for implementing a strategy is to use a well-known security framework for guidance.
At the most basic level, the Center for Internet Security maintains the top 20 critical security controls that every organization must implement to protect their data#2. An organization can use this list to quickly get a high level overview of their security program maturity. The top security control often takes many people by surprise – managing an “Inventory of Authorized and Unauthorized Devices”. Organizations need to manage access to the network and keep all of those systems up to date. In our penetration testing engagements, it is often the forgotten server or the unauthorized test machine that provides the initial foothold on the network. Now how many organizations do you know that are not tracking all devices on their network?
For a more detailed healthcare security strategy, the National Institute of Standards and Technology (NIST), offers the “Framework for Improving Critical Infrastructure Cybersecurity”#12, the result of an Executive Order for managing cybersecurity risk. This freely available framework provides cost-effective measurable steps that an organization can use to protect their data. At the heart of the framework are the following high-level functions: Identify, Protect, Detect, Respond, and Recover. Each function contains a series of actionable security controls. The framework also contains a tier structure to measure the maturity of a security program from “Partial” (Tier 1), to “Risk Informed” (Tier 2), to “Repeatable” (Tier 3), and finally “Adaptive” (Tier 4). Health and Human Services makes this even simpler for healthcare environments by providing cross-references between the NIST framework and the HIPAA Security Rule#8.
2. Risk Analysis – A comprehensive Risk Analysis should include a review of the organization’s security strategy, policies, controls, and include actual security testing to measure the effectiveness of the program. This task is often completed by trusted third parties, but can also be accomplished by knowledgeable staff. Not only is this a HIPAA requirement within the Security Rule, but it is also essential to understanding the risks within a healthcare environment and implementing solutions. This is a way to evaluate the security program and should be a component of the overall security strategy.
3. Education – Implementing a successful security program is only possible with the right people in place. This can be difficult as there is a lack of skilled individuals with predictions of a shortage of 2 million cybersecurity professionals by 2019#10. Training your staff is essential to improving knowledge and staying ahead of adversaries. Utilizing trusted partners is often a cost effective way to fill those advanced roles or complete complex projects. Encouraging participation in local ISSA chapter meetings, 2600 meetings, and OWASP chapter meetings, taking courses, and attending security conferences such as local BSides conferences all increase the skill levels of the team. Fostering an environment of knowledge sharing helps raise the skill levels and also is great for team building. Education is so important that it is even one of the Critical Security Controls: “Security Skills Assessment and Appropriate Training to Fill Gaps”#2.
4. Encryption – It should go without saying that all Protected Health Information (PHI) needs to be encrypted, but breach trends show that organizations still need work in this area. Encrypting laptops is absolutely needed, but workstations and flash drives need to be encrypted as well. PHI needs to be encrypted in transit as well as in storage. Once again, “Data Protection” is a Critical Security Control#2.
5. Security Testing – Performing penetration testing on the organization and its applications are necessary for finding security problems before an intruder finds them. Trusted third parties usually perform these tests and larger organizations often have internal Red Teams that continuously test the environment. Discovering these security holes is just the first phase of this process. The second and lengthier phase is putting a plan in place for fixing the problems. “Penetration Tests and Red Team Exercises” is another Critical Security Control, thus highlighting its importance#2.
All of the described solutions are crucial components of a well-developed security strategy. Without a plan in place, organizations will endlessly play a cat and mouse game, jumping at the next threat, but not creating a framework to contain all hazards.
Closing
With over 174 million records lost to date, healthcare breaches are a growing epidemic that needs to be addressed. Hacking and ransomware are two growing threats continuing to slam the healthcare industry. However, there is hope as breaches due to physical theft have been declining in recent years. Theft used to be the largest cause of healthcare data breaches and if this threat can decline, so can other data breach sources. Comprehensive security strategies and risk analyses will reduce the risk of hacking, ransomware, unauthorized access, and other threats. Healthcare breaches affect every one of us and this problem will not fix itself. So let’s get to work and secure this information because each of us has only one identity and it needs to be protected.
Bio
Jon Sternstein, CISSP #378687, is the Founder and Principal of Stern Security, a data security company headquartered in Raleigh, NC. Jon is the co-chair of the Privacy and Security Workgroup at the North Carolina Healthcare Information & Communications Alliance (NCHICA) and is a former healthcare security officer. Jon is a member of the ISSA Raleigh Chapter, and an organizer of the BSides Raleigh security conference. He may be reached at the following page.
1. Balakrishnan, Anita. “The hospital held hostage by hackers.” CNBC. February 16, 2016. https://www.cnbc.com/2016/02/16/the-hospital-held-hostage-by-hackers.html.
2. Center for Internet Security. CIS Controls. 2017. https://www.cisecurity.org/controls/.
3. Databreaches.net. Databreaches.net. April 5, 2017. https://www.databreaches.net/highly-confidential-psychotherapy-records-from-maine-center-listed-on-the-dark-web/.
4. Department of Health and Human Services. “HIPAA Administrative Simplification .” HHS.gov. March 26, 2013. https://www.hhs.gov/sites/default/files/ocr/privacy/hipaa/administrative/combined/hipaa-simplification-201303.pdf.
5. Health and Human Services. “$2.5 million settlement shows that not understanding HIPAA requirements creates risk.” HHS.gov. April 24, 2017. https://www.hhs.gov/about/news/2017/04/24/2-5-million-settlement-shows-not-understanding-hipaa-requirements-creates-risk.html.
6. Health and Human Services. Breach Portal: Notice to the Secretary of HHS Breach of Unsecured Protected Health Information . 7 2017. https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf.
7. Health and Human Services. “FACT SHEET: Ransomware and HIPAA.” hhs.gov. 2016. https://www.hhs.gov/sites/default/files/RansomwareFactSheet.pdf.
8. Health and Human Services. “HIPAA Security Rule Crosswalk to NIST Cybersecurity Framework.” HHS.gov. February 22, 2014. https://www.hhs.gov/sites/default/files/nist-csf-to-hipaa-security-rule-crosswalk-02-22-2016-final.pdf.
9. Health and Human Services. “Resolution Agreements and Civil Money Penalties.” HHS.gov. 2017. https://www.hhs.gov/hipaa/for-professionals/compliance-enforcement/agreements/index.html.
10. Kauflin, Jeff. “The Fast-Growing Job With A Huge Skills Gap: Cyber Security.” Forbes. March 16, 2017. https://www.forbes.com/sites/jeffkauflin/2017/03/16/the-fast-growing-job-with-a-huge-skills-gap-cyber-security/.
11. Krebs, Brian. “Hospital Declares ‘Internal State of Emergency’ After Ransomware Infection.” Krebs on Security. March 22, 2016. http://krebsonsecurity.com/2016/03/hospital-declares-internet-state-of-emergency-after-ransomware-infection/.
12. National Institute of Standards and Technology. “Framework for Improving Critical Infrastructure Cybersecurity.” nist.gov. February 12, 2014. https://www.nist.gov/sites/default/files/documents/cyberframework/cybersecurity-framework-021214.pdf.
13. Ponemon Institute. 2017 Cost of Data Breach Study. Ponemon Institute, 2017.
14. Stern Security. “Stern Security – What is Your Breach Risk?” Stern Security. July 13, 2017. https://www.sternsecurity.com.





