Vendor Risk Management Accuracy is all that Matters!
Are Vendors Secure?
If you ask any company if they are secure, most would say “Yes, of course we are!” This is especially true of vendors. No vendor ever says, “No, we’re not secure, but trust us with your data.” Most vendors are not being dishonest, but instead are overly optimistic about their vendor risk management accuracy, security posture and many do not have security staff to increase cybersecurity maturity.
Issues with Most Vendor Management Products
Companies will often look for products to help with their vendor risk management programs. Vendor Management products are generally divided into two categories:
- Self-Assessment Questionnaires: A questionnaire that the vendor fills out and once complete, it gives an automated score of the vendor’s posture.
- Automated Assessments: A solution tool that scans the internet for publicly available details on the vendor in order to determine the security posture.
Both of these vendor management products prioritize getting as many vendors in their system as possible. They then claim they are the best solution because they have the most vendors. Unfortunately, this is meaningless because the results are inaccurate. There is the old adage, “Garbage in, garbage out.”
Self-Assessment Questionnaire Issues
Vendors are unrealistically optimistic about their own security posture, so vendor management products utilizing self-assessment questionnaires give unrealistically optimistic conclusions. Not only are these vendors overly optimistic about their security, but many do not understand the security questions. You hear responses such as “Yes, we have a SOC 2 Audit. Here is the audit from AWS (Amazon Web Services), our cloud provider.” Unfortunately, the referenced SOC 2 Audit only applies to AWS’s own environment, not the application that the vendor may host in AWS. Instead, the vendor actually needs their own SOC 2 Audit for their own application. Another typical vendor response is “Yes, we’re secure because we host our application at AWS.” However, AWS claims zero responsibility for the security of the vendor’s application, as they only provide the platform to host it.
A vulnerability scan is not the same as a penetration test. Often vendors are asked if they have penetration tests performed on their solution and many will say “Yes, we have penetration tests performed every week!” However, they are referring to automated vulnerability scans, not comprehensive penetration testing that encompasses a very detailed manual and automated examination of the solution. If a vendor is filling out a questionnaire that asks them if they do penetration testing on their application, many will incorrectly say “Yes” even if they only do vulnerability scans.
Vendors will often say “Yes, we have a Security Officer” and will designate the most technically savvy person in the organization as their “Security Officer.” However, this person may not be a security professional at all. Sometimes this “Security Officer” is simply an IT support person or a project manager for the company. While this may vaguely provide a “check in the box” for compliance, it is not accurate and does not help the overall security posture of the organization.
Thus the vendor management solutions that rely on these self-assessment questionnaires often have inaccurate results that give their customers a false sense of security.
Automated Assessment Issues
Automated Assessments are fast and give almost immediate scores that supposedly represent the security posture of the assessed organization. These products rely on scanning the internet for publicly available information in order to give a risk rating for a company. While these are very quick, professionals know that they are highly inaccurate. It is like looking at a house on Google maps and determining how secure it is. Sure, you may see a broken window in a grainy picture or a bad neighborhood from a crime map, but you don’t really know how secure the building is.
These products have numerous pitfalls. For example, consider a vendor offering visitors a public wireless network which is completely segmented on an air-gapped network separate from the corporate network. Automated products may see that network and say that it looks like an insecure network which reduces the security posture of the vendor even though this network has nothing to do with the company or its security. Another example is that some of these automated products will look at a company’s public website, find an issue on the site such as a weak SSL certificate, and claim that the vendor has a low security posture. However, the corporate website may have nothing to do with the product/device that the vendor sells.
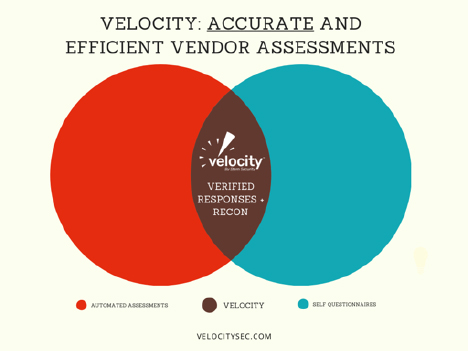
Velocity: The Solution to Vendor Risk Management Accuracy
The standard vendor management accuracy solution options are clearly broken. On one side of the spectrum, you have automated assessments that give fast results that prioritize speed and volume. On the other side of the spectrum, you have self-assessment questionnaires that prioritize convenience and volume. Both of these options produce highly inaccurate results because the data is not verified.
Velocity was created to fix this broken system. Velocity prioritizes Accuracy and Efficiency over volume. A team of security professionals verifies all vendor data in the system before we provide a verified security score and vendor report. Our system utilizes questionnaires and public reconnaissance in order to gather the data, but everything requires verification and supporting documentation before it gets a stamp of approval.
While the inaccurate vendor risk management products may provide a quick check in the box for compliance, they are not providing security and instead are giving customers a false sense of security with regard to their vendors. If we are going to flatten the breach curve and reduce the amount of vendor breaches, we need to accurately measure risk. The time has come to choose accuracy, security, and efficiency over volume and bare minimum compliance.
For a look at how Velocity helps companies manage their security posture and vendor risk: